REPORT: Philippine Army source of cyber-attacks vs. media outfits
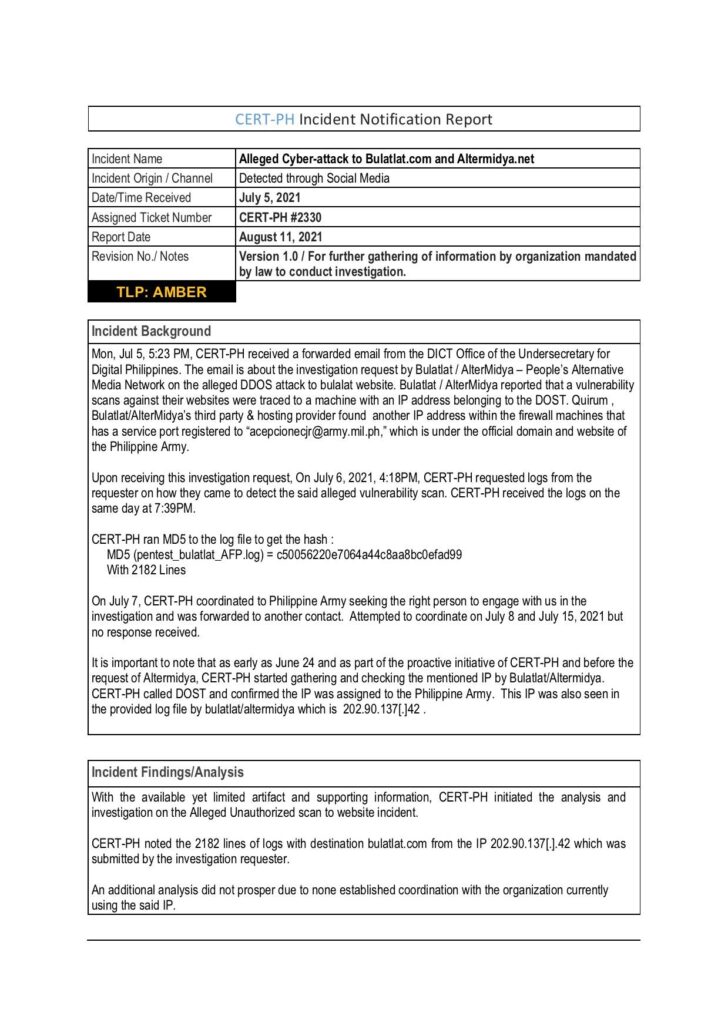
An internet protocol (IP) address assigned to the Philippine Army was the source of cyber-attacks on media websites Bulatlat.com and Altermidya.net, a government agency confirmed.
Bulatlat and Altermidya said the Computer Emergency Response Team (CERT-PH), an agency of the Department of Information and Communications Technology (DICT), finally gave them a copy of its initial findings confirming earlier reports state agents were behind the attacks on their websites.
In an August 11 report, CERT-PH said its analysis and investigation revealed that IP address 202.90.137[.].42 that conducted unauthorized vulnerability scans of the said websites, was assigned to the Philippine Army.
“CERT-PH noted the 2182 lines of logs with destination bulatlat.com from the IP 202.90.137[.].42, which was submitted by the investigation requester,” part of the report said.
A vulnerability scan seeks potential weaknesses in the targeted network without permission from the system owner.
READ: Group reveals attacks on media and human rights websites
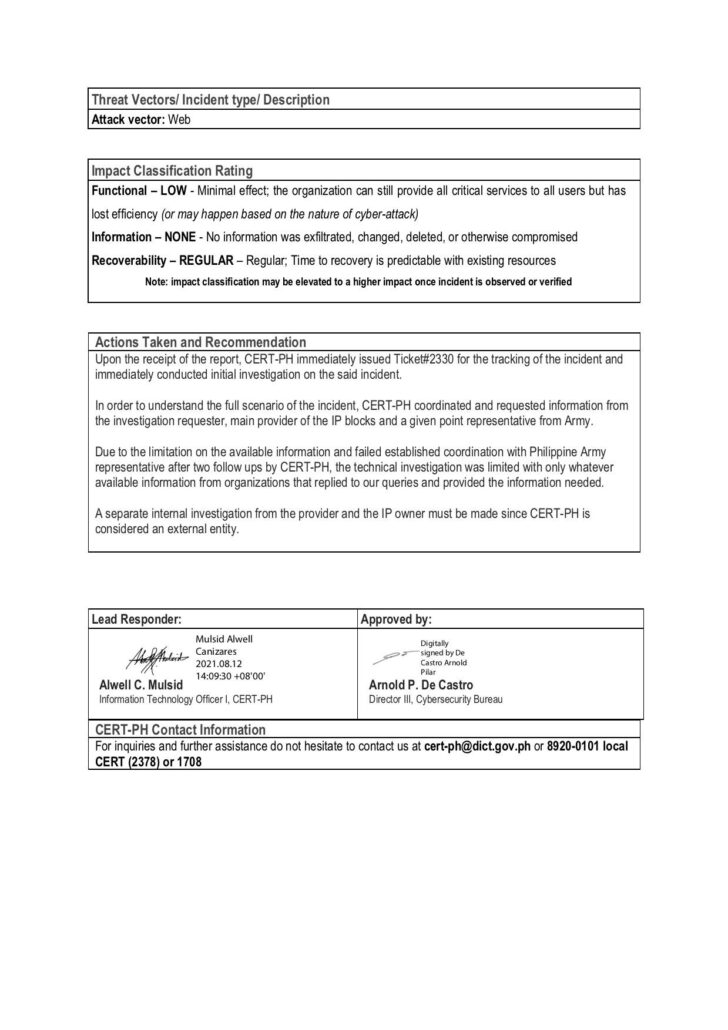
CERT-PH’s report said additional analysis of the incidents did not prosper due to Philippine Army’s refusal to reply to requests for “coordination.”
In a joint statement, Bulatlat and Altermidya said CERT-PH’s report validated findings made last June by their hosting provider, Sweden-based Qurium Media Foundation.
The media outfits said the Armed Forces of the Philippines at the time feigned ignorance and issued a statement claiming it upholds press freedom.
The DOST, which provides the infrastructure to the Philippine Army, also refused to reveal the agency behind the IP space and to this day has not communicated with Bulatlat and Altermidya regarding its promise to ask the DICT for an independent probe, despite repeated requests.
“As of today, we have not received any communication from the DOST regarding its investigation, which we requested a copy of. We tried reaching out to them via office phone and email, but we have yet to receive a response,” Bulatlat and Altermidya said.
The media outfits said they condemn the Philippine Army for carrying out cyber crimes against independent media outfits.
“We take offense at the duplicity they have shown regarding this incident – publicly professing respect for press freedom but launching vicious digital attacks, and never cooperating with other government agencies,” the outfits said.
Bulatlat and Altermidya also expressed disappointment with the DOST for “covering up for the Philippine Army.”
“DOST should not allow its infrastructure be used to suppress the truth, and should impose penalties for agencies found to commit abuses,” they said. # (Raymund B. Villanueva)